
Friday, May 12: WannaCry knocks!
Friday, May 12 seemed to be another typical day for most people as they began their day crazily waiting for a fun-filled weekend; but as the day progressed; many companies across the world realized most part of their working day, which was scheduled to be relaxing in anticipation of a weekend, is going to be spent dealing with a ransomware attack known as WannaCry.
Post Quick Links
Jump straight to the section of the post you want to read:
The biggest ransomware attack ever? The extent of damage
The biggest ransomware attack ever? The extent of damage
WannaCry is not just yet another programmed ransomware, dedicated to making money using dishonest ways; but it is the biggest ransomware attack ever. The attack was massive and prevalent around the globe and was reported to infect the telecom networks in Spain, contain hospitals in the United Kingdom, and force a car manufacturer to shut down a factory.
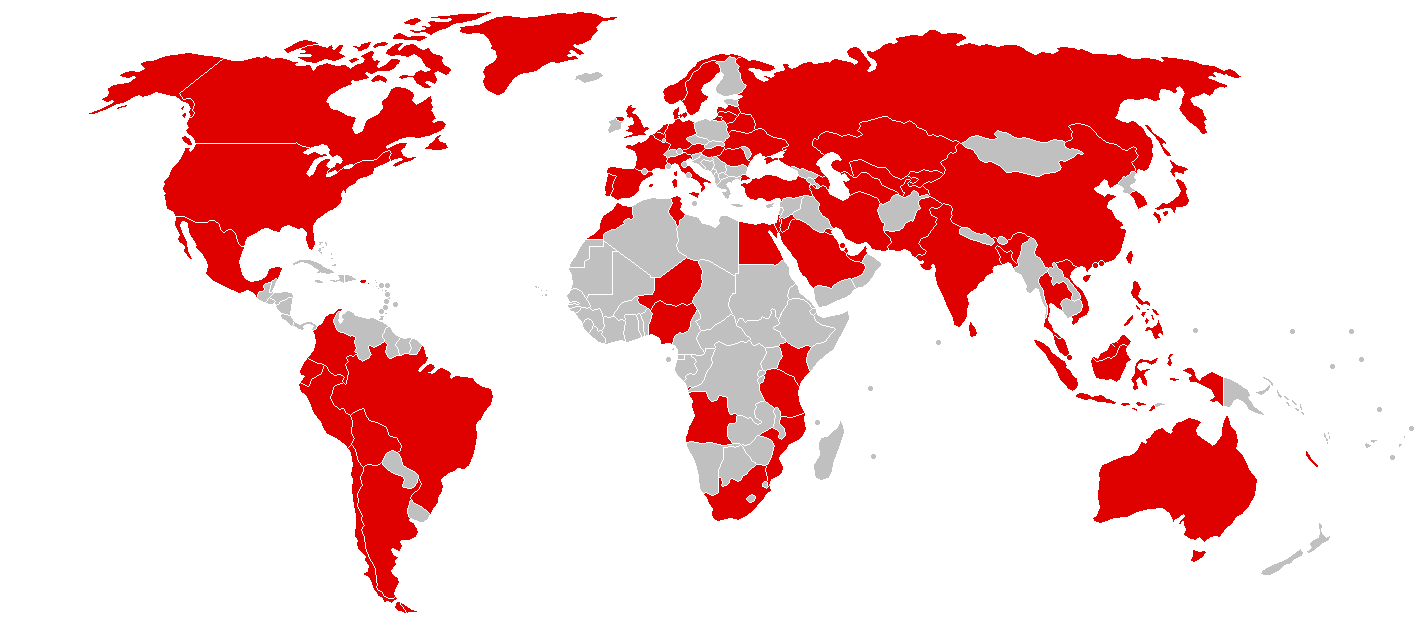
It was reported the ransomware which targeted computers that run on the Microsoft Windows operating system in the form of first encrypting data and subsequently demanding ransom payments in the Bitcoin cryptocurrency, infected over 230,000 computers in over 150 countries.
Accidental Hero: @MalwareTechBlog
Accidental Hero: @MalwareTechBlog
However, much of the potential damage of the ransomware attack was for the time being contained by the efforts of a 22-year-old security researcher, with the handle @MalwareTechBlog on Twitter. The researcher found the attacker accidentally and included a kill switch in the software, which allowed the owner of a particular website to stop the attack.
But the victory over the evil could be short-lived; since experts say WannaCry is very much likely to be upgraded with even more vulnerable features and continue to spread its heat in a different form. The improved version could be challenging enough to counter. However; researchers are working on measures to contain any risks.
So, the risk is not fully contained and given the extent of damage it already caused; it requires little introduction that if you are connected online; either as an individual or as a business, you need to be extra careful.
Among all the bad guys out there dedicated to spoiling the Internet, ransomware is turning out to be the clear winner. Cisco’s annual cyber security report has some alarming statistics.
The increased risk of privacy and manipulated mechanisms to trick users into paying is making ransomware a very important matter of concern for users. Ransomware, experts say, need to be contained or they might bring more issues.
- It’s growing at an annual rate of 350%
- The FBI estimates the annual global market to be around one billion dollars
No longer unprecedented in scale: Time for layers of security
No longer unprecedented in scale: Time for layers of security
In order to counter the risks of ransomware; it has become extremely important that businesses and individuals work on some of the strategic factors and apply layers of security in order to stay safe and secured from any type of ransomware. This list is populated with key measures you need to read now and take an action to stay secured from online vulnerability.
Small and Individual Businesses should..
Small and Individual Businesses should..
Always back up – When you are attacked by a string of surprising ransomware or simply an unruly ransomware or if your hard drive suddenly dies up, backing up your data is perhaps the most important thing you need to do. However, remember; backing up your valuable data alone cannot guarantee complete security if you are not taking other precautionary measures.
Know when to work as privileged and when as non-privileged – Always make sure that you configure access controls like network, file and directory permission with the least privilege principle in mind. Most of the users in charge of development and design do not necessarily need admin access. So, always make sure to demarcate the line of authorship of system administration. While working as non-privileged user does not always make you immune to WannaCry ransomware; it can, of course, contain the ransomware to carry out risky attacks such as deleting shadow files of the system
Because the ransomware has been extremely hostile to Windows operating system, it is crucially important that you install the Windows updates MS17-010. You should turn on the Windows Automatic Updates if you have not yet.
It is also important that you use a professional antivirus. It should automatically scan your computer for infected files and folders. A good antivirus is extremely important in today’s evolving marketplace. Anti-malware is also good option for small business and individual to protect themselves from malicious attacks of ransomware
Big organizations should..
Big organizations should..
- Apply the latest Microsoft security patches for this specific flaw and back up their most deciding data.
- Make sure that all the emails are properly checked
- Educate existing workforce on how to identify scams, malicious software, links, emails and etc
- Always keep updated about latest vulnerabilities and stay protected using the latest security guidelines
Ive been attacked and asked to pay the ransom
I’ve been attacked and asked to pay the ransom. Now, what?
Do not ever pay anything to the attacker. According to experts on the subject, there is no evidence of the hackers giving people back their files
For small businesses and individuals, it is worthwhile to contact local IT support services authority




About the author
Expert
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Related Articles
How to choose the best proxy for Brand Protection?
Here is a guide on how to secure your brand with reliable proxies in 2020. Know how to choose the best proxy for brand protection
HTTP Headers: What Are They?
Here we would have HTTP headers explained in good details, their purposes, and why it is important to optimize them during web scraping. Know More Here